Advance usage of SSH
What is Authentication?
Authentication is the process of taking an identity and using some form of verification, the identity can be verified as being legitimate. Privacy and Confidentiality.
Why Authentication?
it is used for users..
- Privacy
- security
- Confidentiality
Popular Types of ssh Authentication
these types are the most general and used by many users
- Password
- Public key
Eshtablishing a passwordless connection with the remote host using ssh
here's the image explaining the working of Public key authentication mechanism in ssh-
What generally happens?
When the user first connects to the server via ssh,the client asks the user whether to trust the server or not , if the user says yes, then it saves the server hash into a folder called known_hosts.
Hence, the next time the user connects to the same server the promt will never appear
There are many ways to authenticate client, those are highlighted in the image provided below,
note--in the images provided redram is server and dragonram is client
Step 1
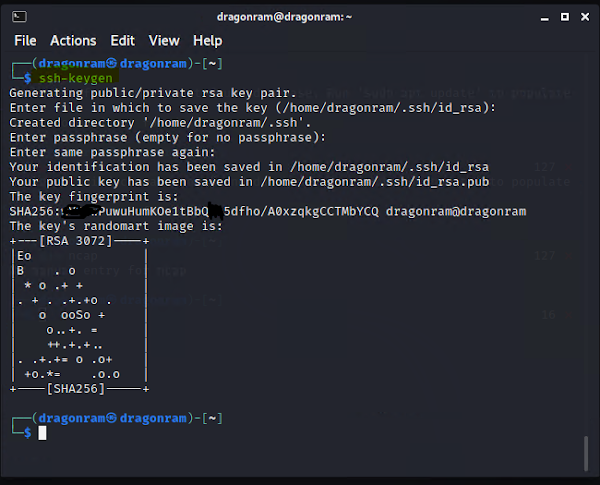
Generate keys in the client and server
passphrase is used to secure the keys with password.
Step 2
Before going to step 2 lets see what happens if we try to login to server
The server tries to search for the stored keys, if any.
step -2 Providing the server with clients key.
we have to login in into server and give are keys in a folder named authorized_keys(/home/user/.ssh/authorized_keys) and alloting permissions to the file.
Step -3
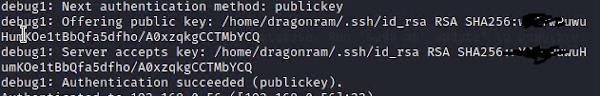
Now exit, and login again
connection succesfull!!









Comments
Post a Comment